

Software Escrow Solutions Explained
Ready for Continuity
You can keep using the deployed application(s) even when your software provider fails. The source code is released to you for updates/ maintenance.

How does it work?
It’s a simple 3 step process that stores and releases the required assets when you need them after a release event.
Store Assets & Hosted Environment
Release Access
Immediate Use of Deployed Environment
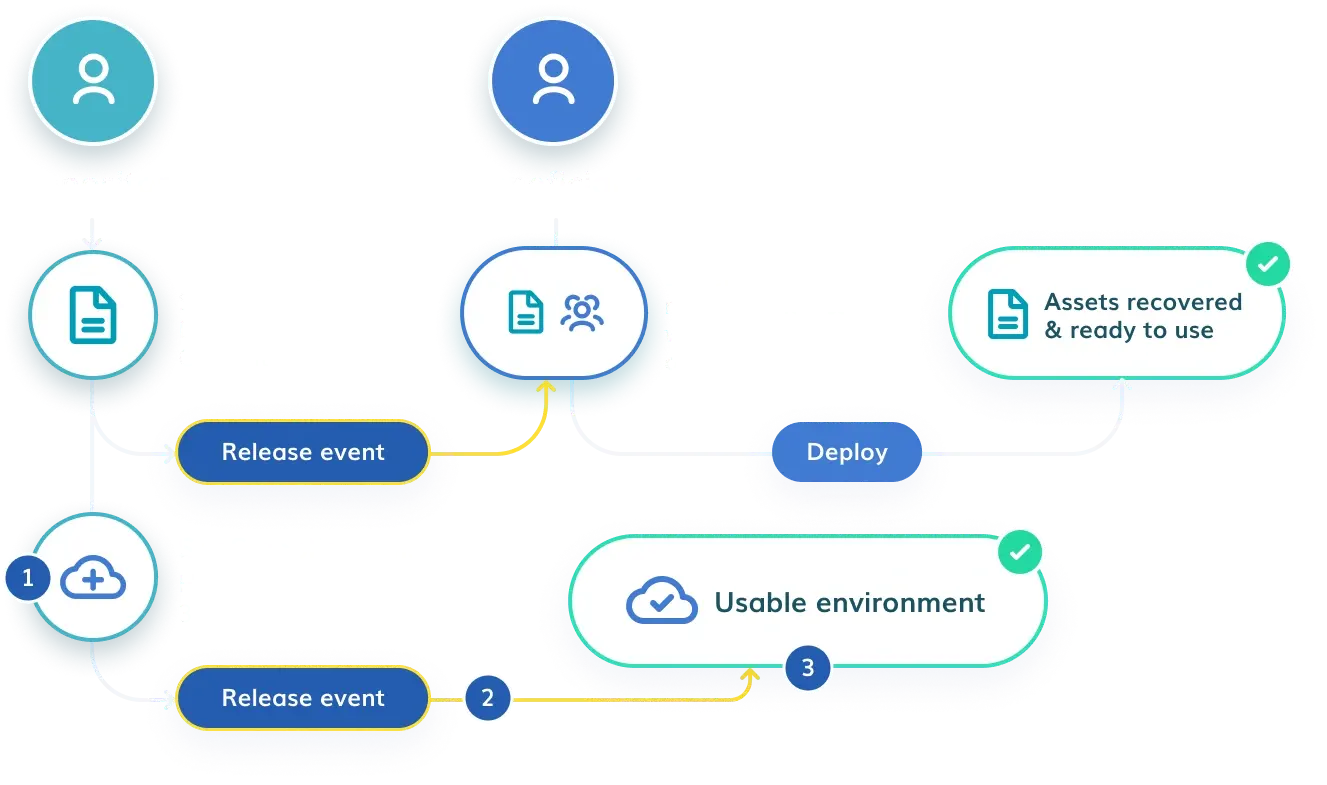
Ready for Continuity
Who does what?
| Role Responsibilities | Depositor | Codekeeper | Beneficiary |
|---|---|---|---|
| Prepare Deposit Materials: Source code, Data, Documents, Deployment scripts, Credentials, etc. |
|
- | - |
| Deposit Hosting Environment access & 3rd party dependency access. |
|
- | - |
| Take Deposit & Store Materials | - |
|
- |
| Update Deposited Materials |
|
- | - |
| Store Updated Materials | - |
|
- |
| Release Conditions Validation | - |
|
- |
| Release Materials | - |
|
- |
| Use Deployed Enviroment (No Downtime) | - | - |
|
| Redeploy Materials for Maintenance | - | - |
|
| Support Redeployment & Maintenance | - |
|
- |
Ready for Continuity
Recovery & Continuity Support
Ready to help when you need it!
Codekeeper has a network of industry specialists available that can help even when your software is very specific or even unique to your company.
Recovery Heroes
Internally we call them our Recovery Heroes, which can help with: redeployment, maintenance, data migration, and many other services you may need when recovering from a software release situation.
Ready for Continuity
SaaS Escrow

Includes all Software Escrow features so that you can also maintain the deployed applications.
Protect Hosting Environment
Include the up-and-running applications into the escrow. Also include any 3rd party dependencies.
Immediate Recovery
No downtime because the running applications are secured in the escrow.
Recovery & Continuity, what’s the difference?
| Feature comparison | |
|
|---|---|---|
| Securely handle and store IP (source code, data, etc.) |
|
|
| Solid escrow agreement |
|
|
| Legal process when release is triggered |
|
|
| Automated and up-to-date deposits |
|
|
| Integrated with developer workflows (no coding required) |
|
|
| Ready for Recovery |
|
|
| Protect Hosting Environment(s) |
|
|
| Include 3rd Party Sub-Services |
|
|
| Ready for Continuity |
|
Do you have requirements that are not listed above? Contact our Customer Service to get custom solutions.
These companies already secured their software continuity.
Will you start today?
Best price guaranteed
No hidden costs

Introduction to Software Escrow: A Guide
E-BOOK
12 pages

Download this ebook for free!

*E-book available only in English



A session with our expert