Meet new operational resilience requirements with software escrow
Your critical software dependencies have become your greatest operational risk.
And now, regulators hold you accountable for these vulnerabilities.
Without proper controls, you risk non-compliance penalties, business disruption, and reputation damage.
These regulations are coming for your vendor risks

New EU cybersecurity law imposes operational continuity requirements on all connected products sold in Europe, effective December 2027.

EU regulators demand documented proof that your IT systems can survive vendor failures and cyber incidents affecting your supply chain.

EU regulators mandate continuous monitoring of software supply chains with mandatory breach reporting when vendors compromise your systems.

Australian financial regulators now hold you accountable for maintaining operations when your critical software vendors go out of business.

US banking regulators expect comprehensive vendor oversight with tested contingency plans for every mission-critical software dependency.

German regulators require critical infrastructure operators to maintain verified backup capabilities for essential software systems.

International standards demand documented business continuity procedures, including measures to protect against third-party vendor failures and maintain access to critical software systems.

Data protection regulations extend your personal liability to include security failures and data breaches by any software vendors processing personal data on your behalf.

Compliance audits require demonstrable oversight and control effectiveness across all software subservice organizations supporting your operations.

Healthcare regulations impose strict security controls and breach notification requirements for any software applications handling protected health information.

Enterprise risk management frameworks stipulate quantifiable resilience metrics and recovery timeframes for all critical technology dependencies.

UK PRA guidelines require due diligence and continuous risk monitoring for all outsourced technology services by regulated firms, with enhanced due diligence for material outsourcing arrangements.
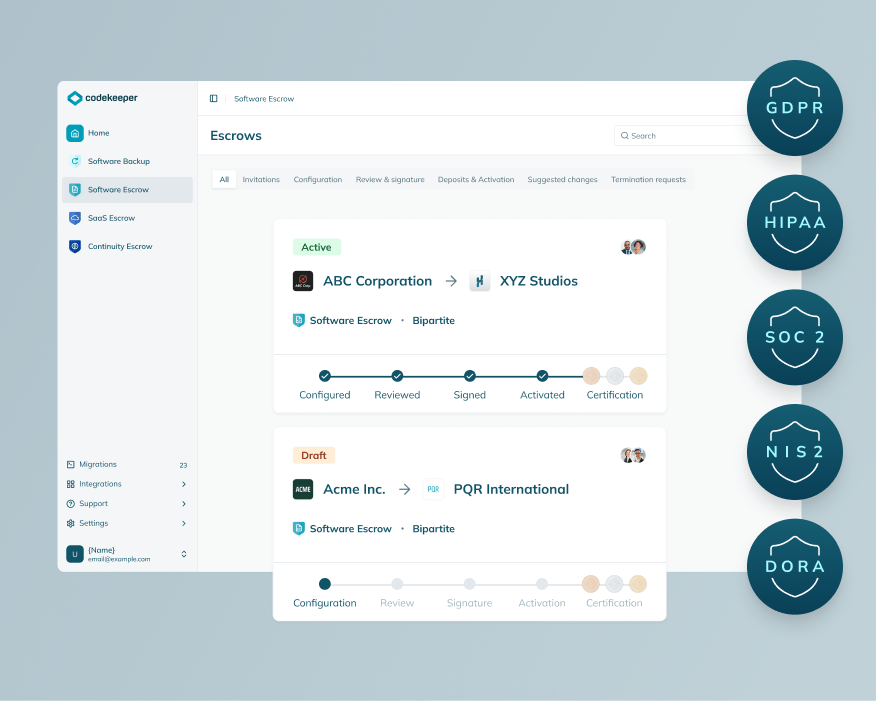
Let us help turn your software risk into operational resilience
How software escrow builds software resilience
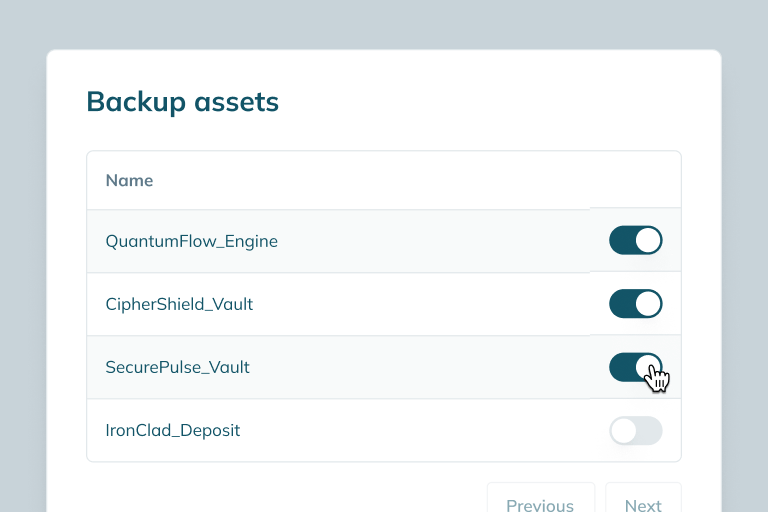
(99.9% uptime, MTBF metrics, failover systems)
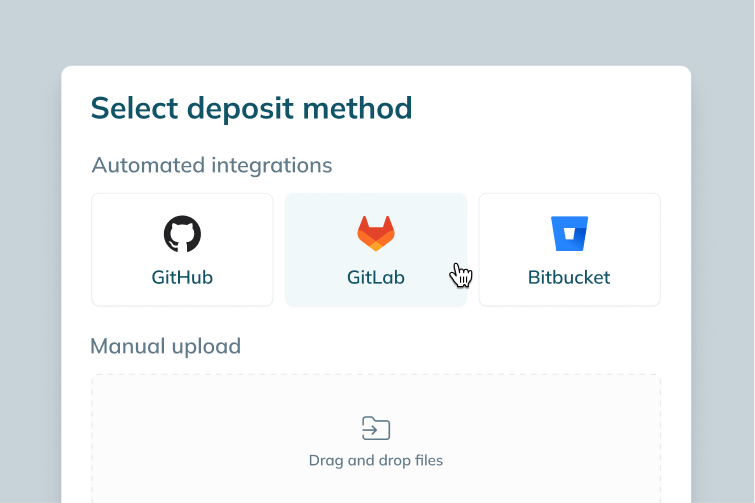
(vendor assessment, API dependency tracking)
(BCP testing, failover plans, tolerance levels)
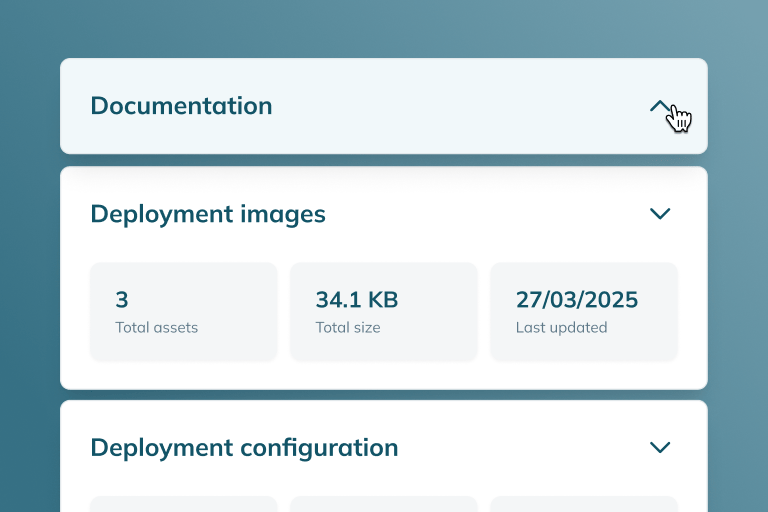
(immutable backups, RPO/RTO controls)