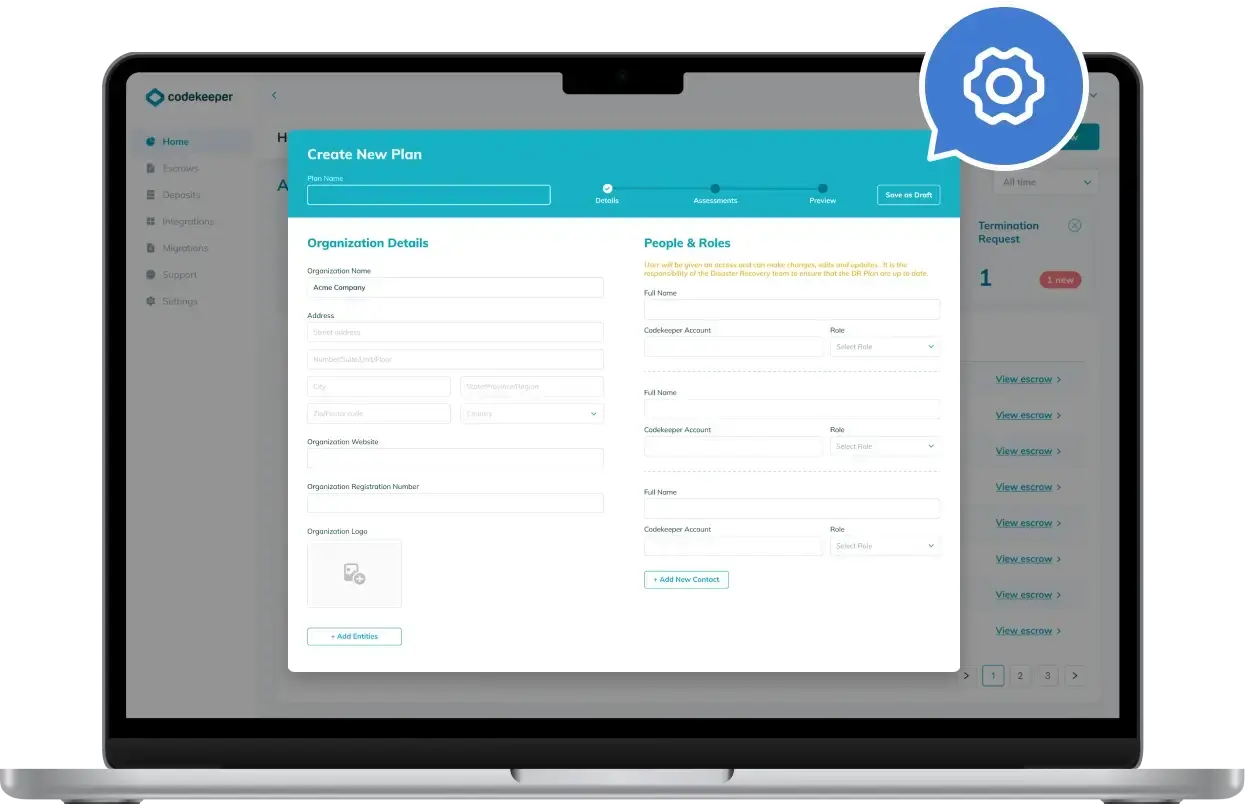
Backup for Internal Recovery
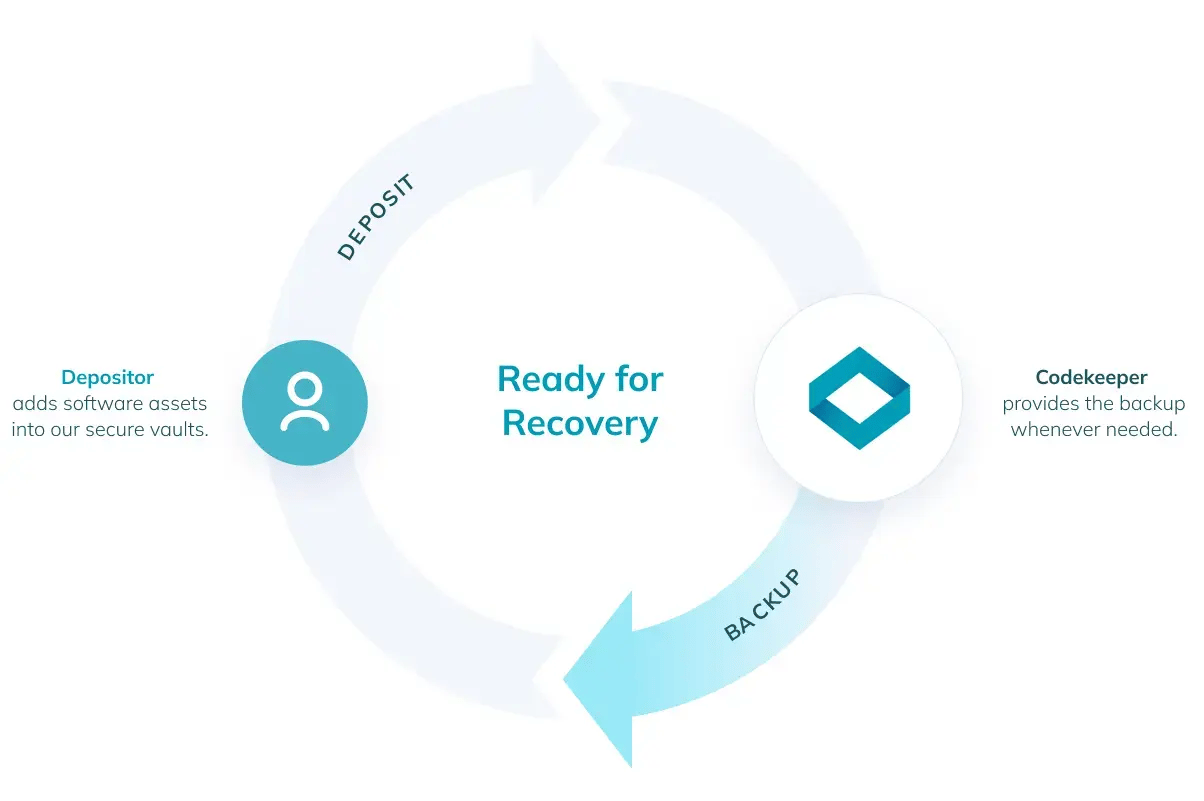
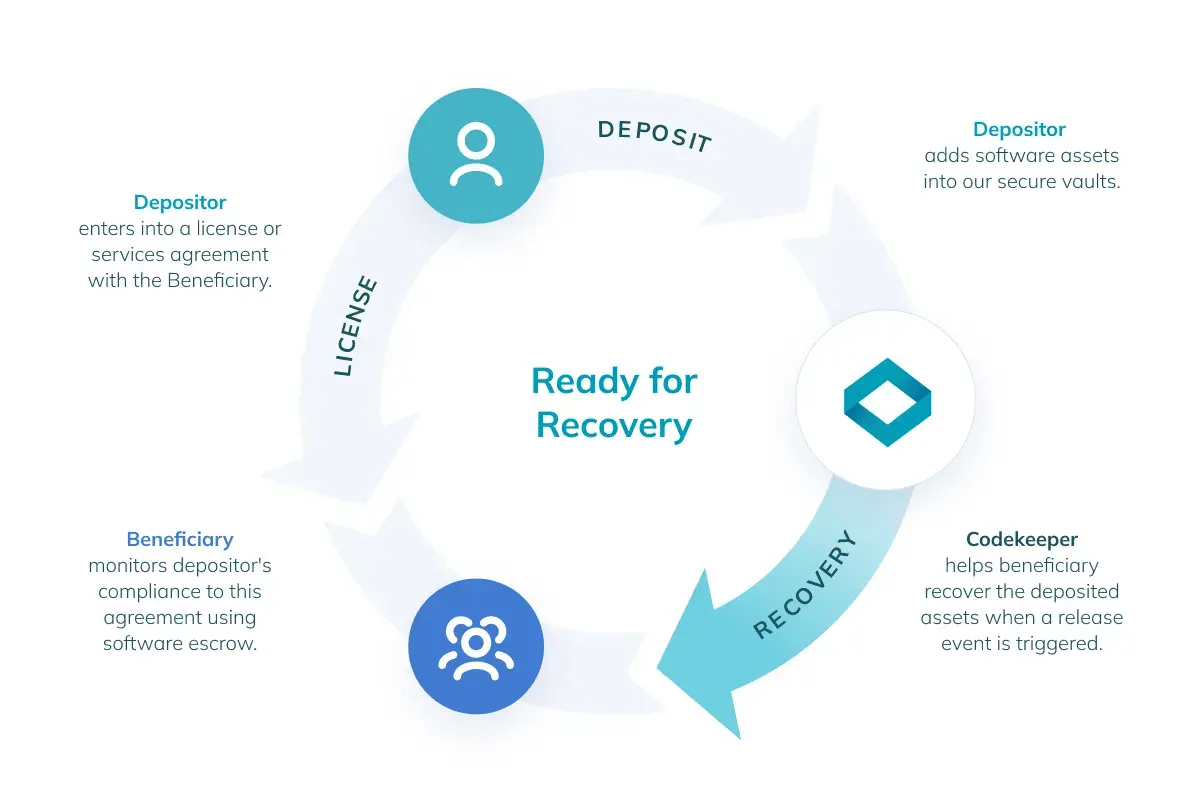
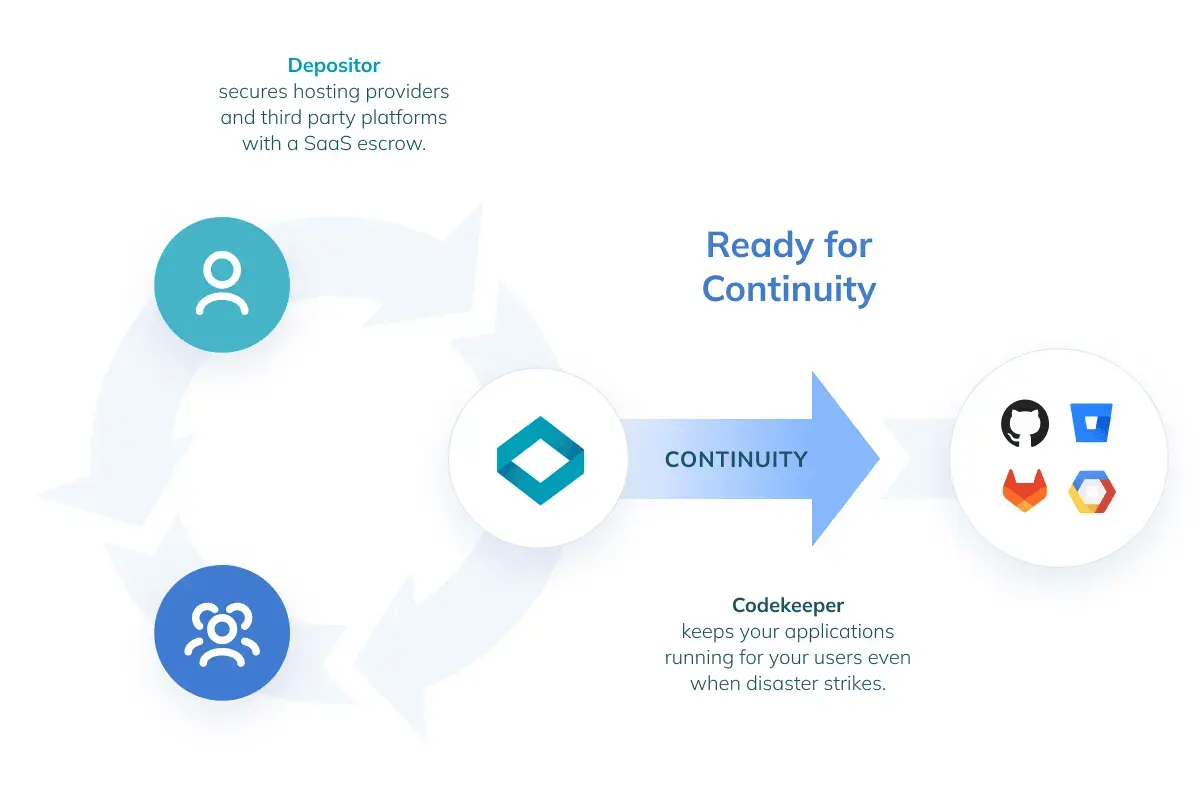
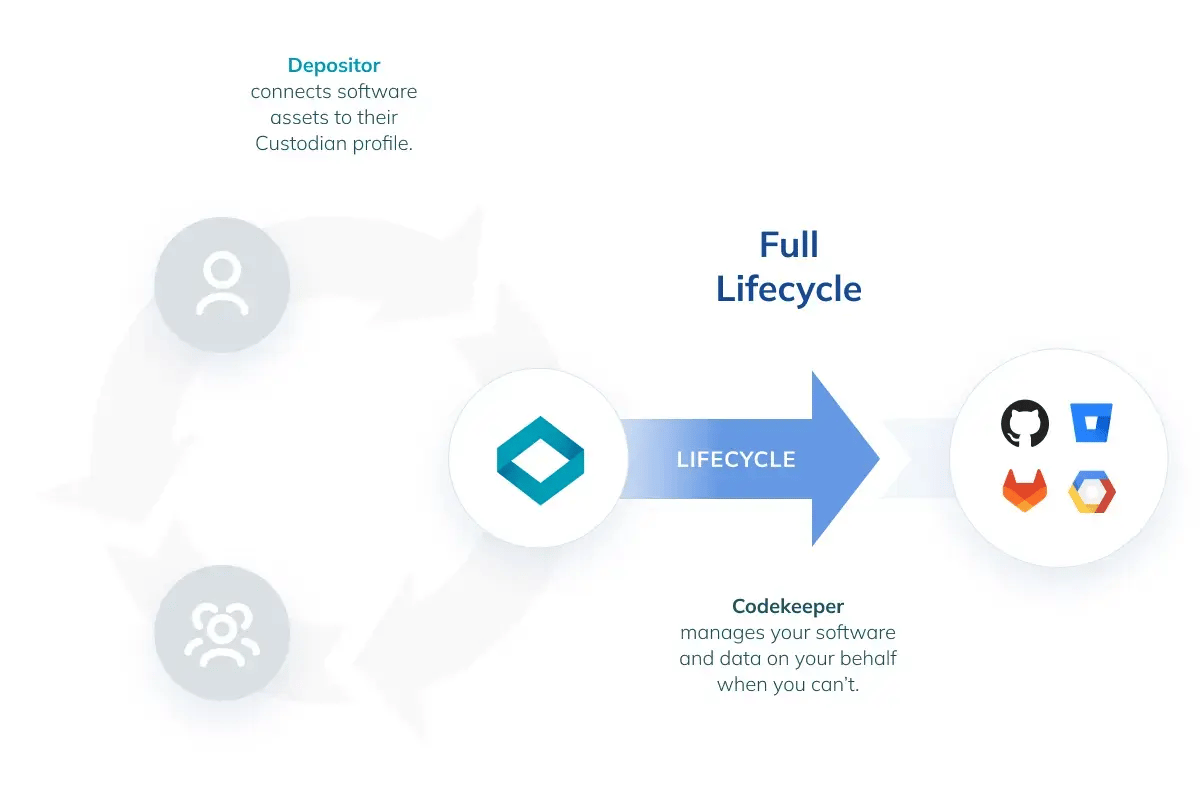
Building upon a solid plan, the next layer of protection involves Backup for Internal Recovery. This solution focuses on safeguarding your internal operations by creating secure copies of all critical software assets.
Regular backups ensure that in the event of a disaster, your business can quickly restore its operational capabilities without significant data loss, using the most recent, uncompromised data.