solutions overview
Manage your software risk with the right control
Close your software resilience gaps with easy-to-use and easy-to-implement Software, SaaS, or Continuity Escrow risk controls. We protect your critical systems so you can promise continuous service to your clients.
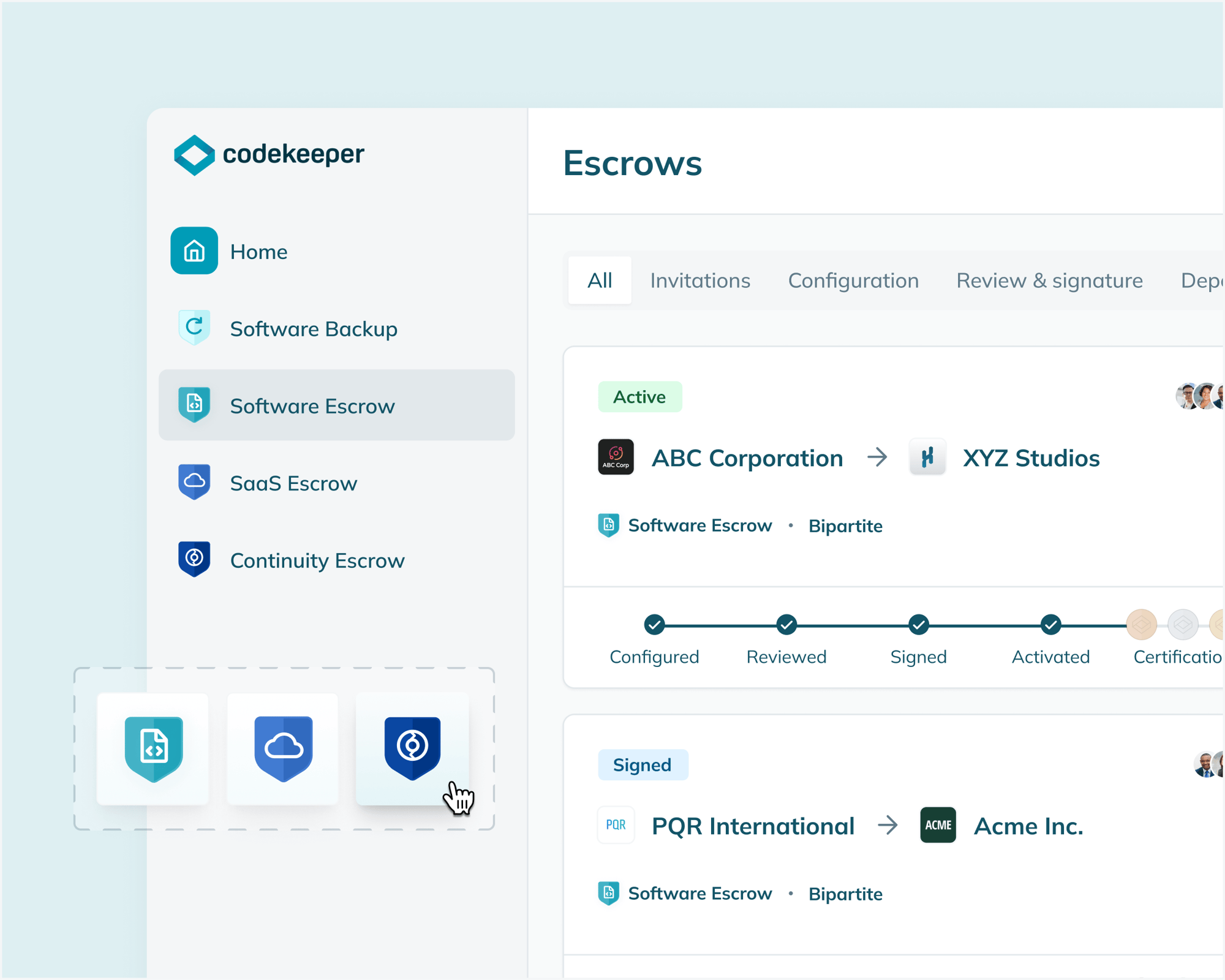
What if modern software protection could guarantee your business continuity?
Traditional escrows weren't built for modern operational excellence
Setting up traditional software escrow is complicated.
You need to verify code, recreate development environments, and make sure everything works together perfectly.
Legal processes are expensive and take too long.
Contract negotiations drag on, and updating agreements takes up valuable time.
Managing multiple escrows is too much work.
You're constantly updating deposits, checking compliance, and managing paperwork.
Software continuity is difficult to prove.
When regulators or clients ask about your software protection, it's tough to show solid proof.
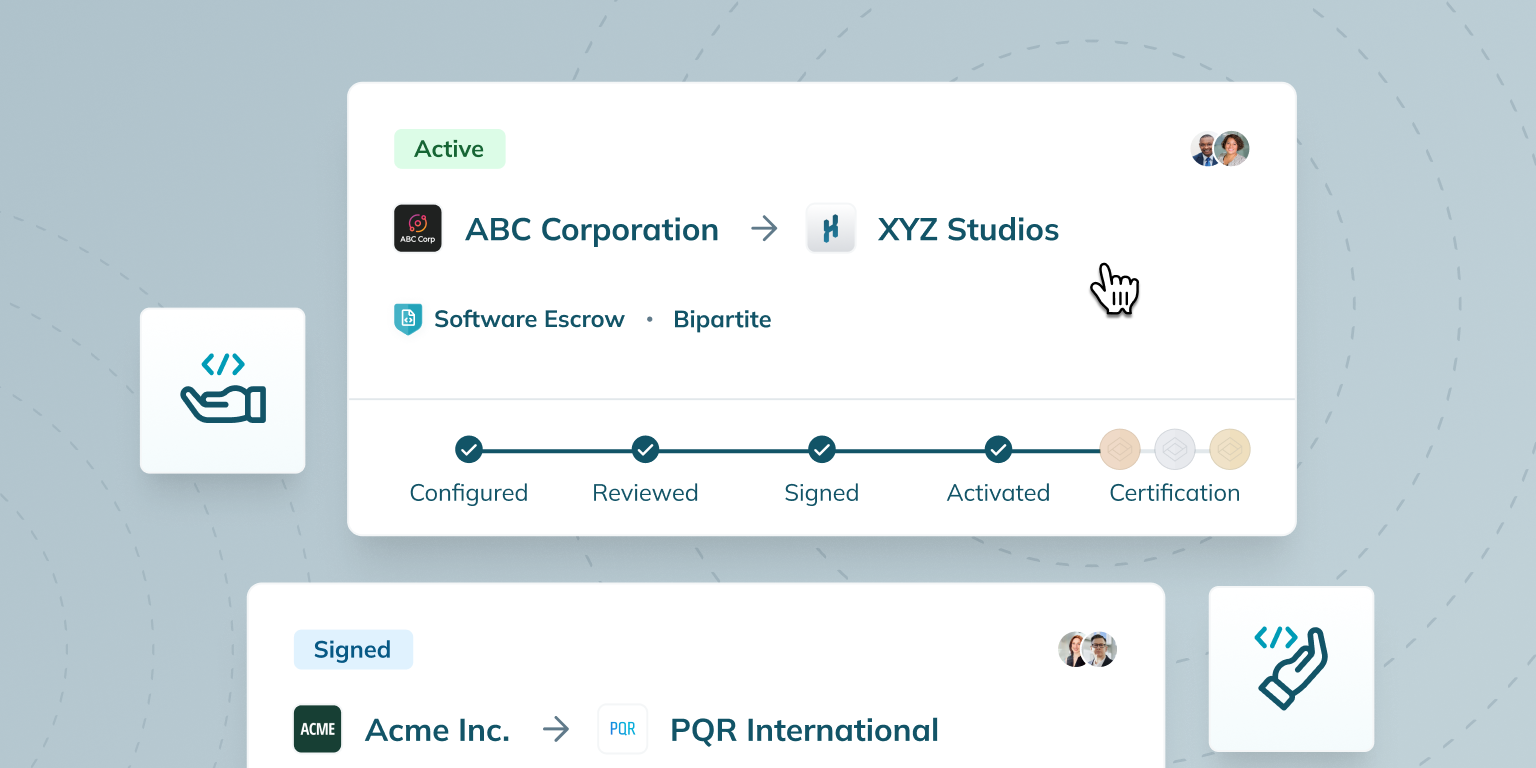
Codekeeper solves the hard parts of escrow — for everyone
We worked with businesses like yours to redesign our escrow process around three non-negotiable client needs:
Easy escrow setups
It shouldn't take weeks to upload and validate assets — Codekeeper connects with your SCMs and auto-syncs every 24 hours to update deposits with no developer effort.
Full legal support
Many users initially worry about pushback from counterparts — our legal team handles 100% of your negotiations and can set up escrow agreements in less than a day.
Certified proof of continuity
We understand the pressure of proving compliance — it’s why we issue instant continuity certificates with every verification.
Let's eliminate your software risk together
While traditional escrows trap you in complicated setups, Codekeeper keeps software protection simple. We help you implement solid risk controls for complete continuity in three easy steps:
1
Select your application type
Before settling on a risk control, we first help you determine exactly what kind of application you need to protect. The Codekeeper vault guards:
On-premises software
Our experts recommend a source code protection solution like Software Escrow for installed software that runs on company servers.
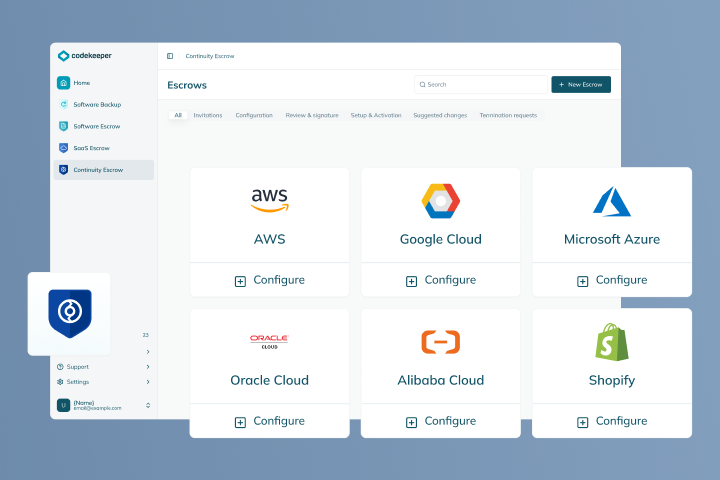
SaaS and cloud applications
If you mainly access your software through remote services or web browsers, you want to look into SaaS Escrow or Continuity Escrow.
2
Choose your protection level
All you need to do is decide whether you want to bring systems back after failure or keep them online through any crisis. We'll help you find the right level of protection and implement your solution.
Recovery
Deposit everything needed to run your software or cloud applications in escrow. If you ever have to redeploy your systems after disruption, you can access your digital assets from Codekeeper's secure vault.
Software Escrow
Learn more
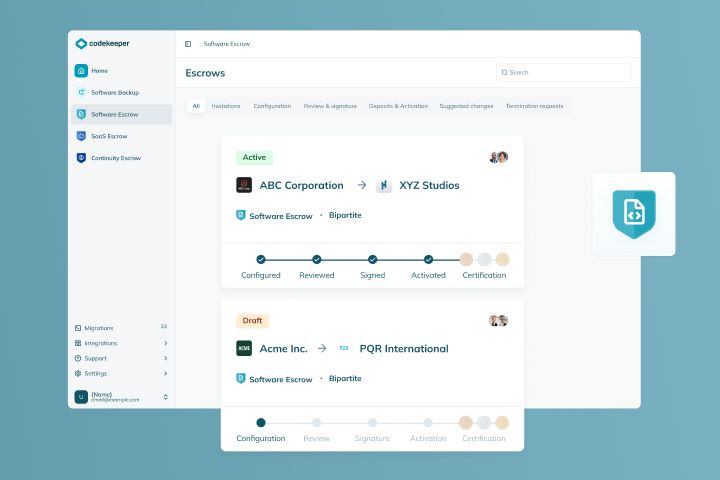
SaaS Escrow
Learn more
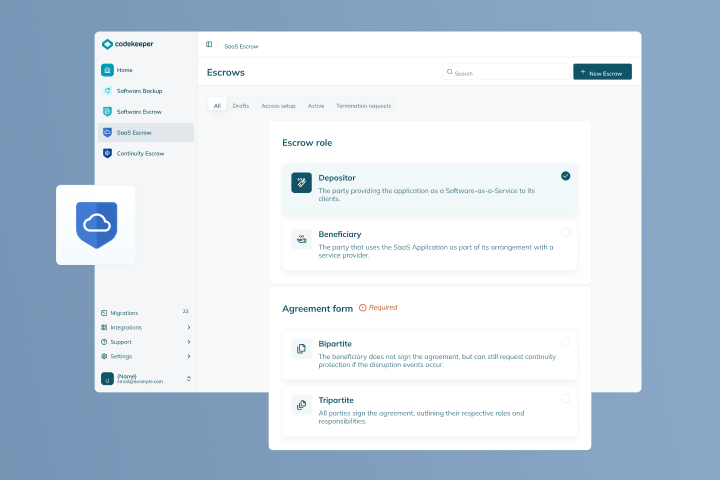
Continuity
Prevent system disruptions entirely by letting us take over service payments when you or your vendor can't. We make sure your key providers are paid on time, every time, so your business never goes offline.
Continuity Escrow
Learn more
Custom Escrow
Request custom offer
3
Get your continuity certified
If you need documented proof that you've taken every step to protect your software, we can execute different levels of verification on your escrows and give you continuity certificates with your results.
Basic validation
We verify that all your assets are in escrow by running free scans whenever a deposit is made.
Automated verification
We do regular automatic content and activity checks to make sure your escrow deposits are up to date.
Full build tests
We rebuild your complete software in a test environment to prove every component works as intended.
Learn more
Your software: Protected , tested , guaranteed to work .
Satisfy clients, auditors, and boards. Save money. And spend less time and effort managing your software continuity — across apps and clients — with Codekeeper's centralized risk controls dashboard.
We make escrow easy for all parties
Compliance
Meet compliance standards and ensure your business continuity.
Satisfy regulators, clients, and stakeholders with certificates that prove your software continuity.
Get compliance due diligence and security audit support from our team.
Let our team handle your recurring vendor screening procedures.


Management
Stay in control of your critical systems and your continuity.
Codekeeper's beneficiary and depositor dashboard access helps you monitor your protection status in real time.
Our support team is available 24/7 to process any escrow events.
Our recovery team is standing by to help implement your disaster recovery plan if there's an incident.
DevOps
We handle the complex parts of software escrow setup and maintenance.
Our technical team offers dedicated support throughout setup.
Connect Codekeeper with your SCM platforms for easy, automated deposits.
Codekeeper syncs with your system every 24 hours to ensure your escrow contains the latest version of your software.


Legal
Our legal team draws up custom escrow agreements with clear release conditions and balanced terms.
Choose between bi-, tri-, and multi-party escrow agreement types.
Establish custom service-level agreements with increased limited liability limits.
Select your preferred jurisdiction to domicile the escrow agreement.
Every day without modern protection multiplies your risk
Basic escrows can't promise software continuity.
Since 90% of traditional escrows fail verification tests, they can't generate auditor-approved proof of compliance or customer-facing guarantees.
Software resilience gaps trigger cascading penalties.
Inadequate business continuity planning leaves you exposed to fines for non-compliance: 2% of your global revenue and €1M in personal liability.
In-house backups open you up to data breaches.
The average enterprise storage and backup device contains at least three high or critical risk vulnerabilities that could lead to significant compromise.
System downtime will cost you more than money.
One software failure could stop your operations, erase years of business growth, lead to revenue loss, and demolish client trust.
Where would software failure destroy you?
Complete a free risk assessment to understand your software continuity risk. You'll list the number of applications you use. We'll calculate your vulnerability and send you a detailed report showing how to protect your business from software failure.
Software continuity = business continuity.
Don't bet your company's future on systems you can't control.
Guarantee your software continuity with:
Enterprise-grade software protection

Set-it-and-forget-it modern escrows

Solid custom legal frameworks
Frequently asked questions
What is source code escrow?
Source code escrow is a risk management service that protects software vendors and their clients. Through a legal agreement, a neutral third party holds critical software assets in encrypted data facilities. This arrangement ensures customers can maintain their business-critical software if the vendor can't do so while protecting the vendor's intellectual property rights.
How does software escrow work?
Software escrow operates through a legal agreement between three parties: the software vendor, their client, and an escrow agent (like Codekeeper). The vendor deposits software assets — including source code, documentation, data, and build instructions — into secure vaults managed by the escrow agent. These deposits are updated regularly to maintain current versions. The escrow agreement defines specific release conditions, such as vendor bankruptcy or discontinued support. If these conditions occur, the customer can request release of the materials. The escrow agent verifies the claim and, if valid, releases the assets to the customer.
How does software escrow reduce business risk?
Software escrow protects business continuity by ensuring access to essential software even if the vendor can't provide support. For custom software investments, it guards against vendor lock-in and potential loss of mission-critical applications by enabling businesses to maintain their software independently or through third parties. The arrangement also helps companies meet compliance requirements while providing documented proof that critical systems are protected.
What is an application in the context of a SaaS escrow?
In SaaS escrow, an application refers to the complete cloud-based software service that customers access and use over the internet. This includes source code, databases, configurations, deployment scripts, access credentials, and third-party integrations.
How does escrow help win enterprise deals?
Software escrow helps vendors win enterprise deals by transforming critical business continuity concerns into competitive advantages. By offering escrow protection, vendors demonstrate professional risk management and long-term commitment to customer success. For enterprise customers, escrow provides documented assurance that their software investments and operations remain protected, even if the vendor faces difficulties. This protection helps satisfy procurement teams and enables faster deal closure — particularly for smaller vendors competing against larger providers.
How quickly can source code protection be implemented?
Most modern escrow solutions can be implemented within 24 hours. We offer 50+ integrations with popular development platforms, which include automatic syncing with Git repositories, cloud services, and deployment systems. In terms of legal frameworks, our expert counsel drafts custom agreements within one to three days — depending on your requirements.


