Software Escrow Assets
Credentials Escrow
Many applications these days rely on encryption keys, certificates and third-party sub-systems that need to be accessed to keep an application running smoothly. Make credentials escrow part of your strategy to ensure operational stability at all times.
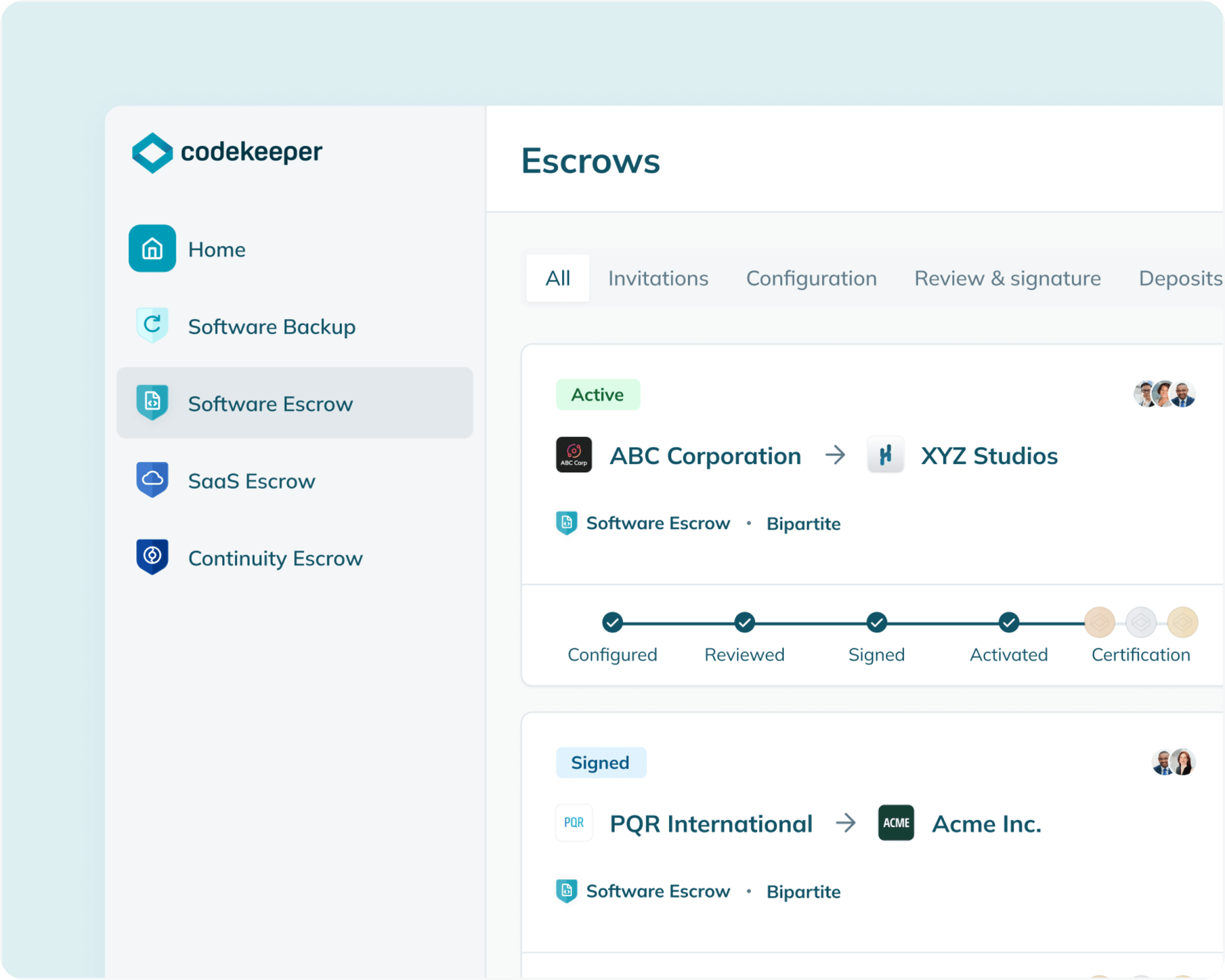
Does depositing a database have to be this hard?
Time consuming manual deposits
Complex deposit procedures
Outdated and incomplete deposit versions
Missing, incorrect and wrong repositories deposited
Developers spending hours outside their workflows
Unsupported Source Code Management platform
Why people choose Codekeeper
Credentials Escrow
Developers love us!
Fully automated and directly integrated with the tools developers use every day to write source code. No longer spending time on making manual deposits into escrows.
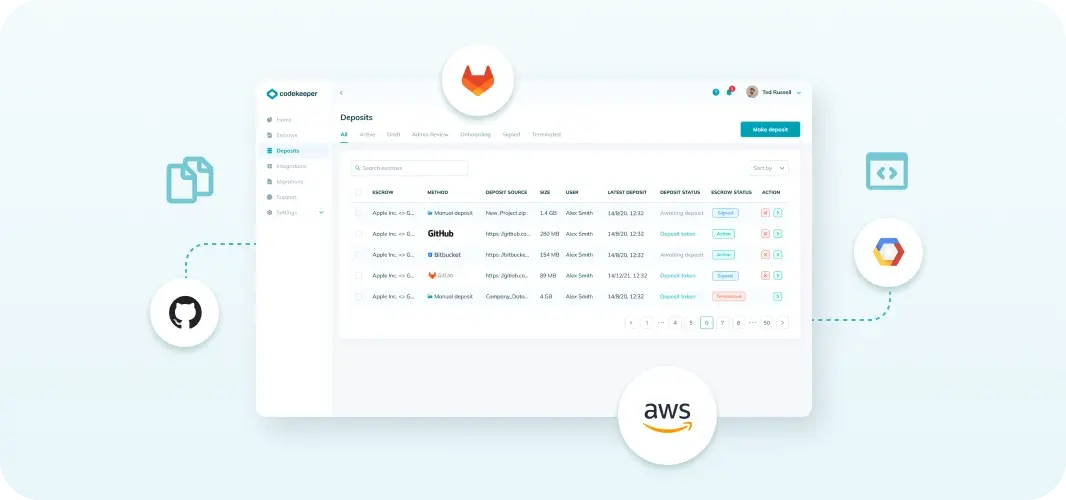
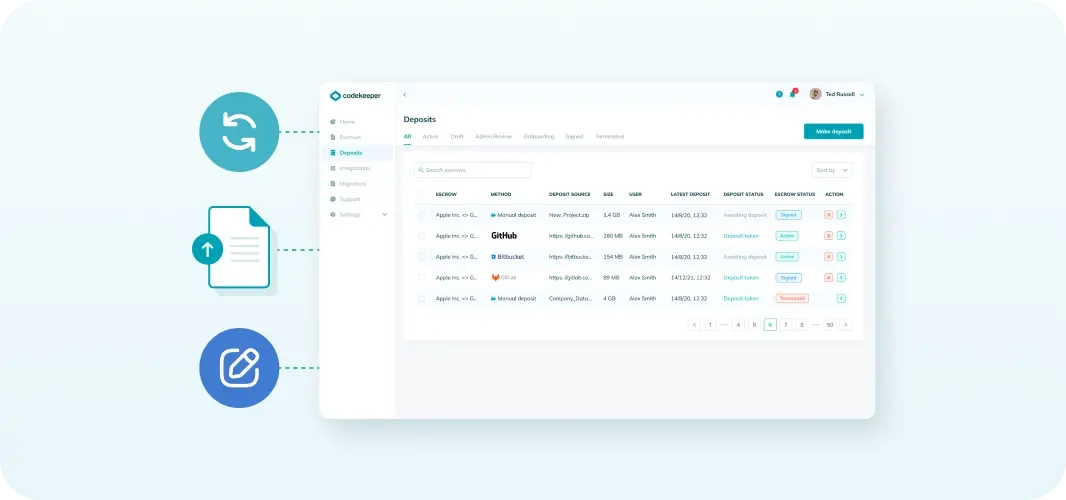
Easy deposit admin
Our user-friendly interface allows you to easily add and manage your repositories. Finally, you won’t need to keep track of and manage new releases, version updates or which repository belongs where.
Integrations library
Recent versions are always deposited within 24 hours, end-to-end encrypted (AES256) and fully automated. We support more than 50 integrations!


Many add-ons available
Need local storage? Or a Data Processing Agreement for GDPR/HIPAA? No problem! Have us verify and certify the deposits.
How it works
Setting up credentials deposits for the escrow is a simple process. Codekeeper works directly with the systems where you currently keep your information.
Integrate the platform of your choice
We support most commercially available environments with 50+ integrations available! See all integrations
For non OAuth integrations we provide a simple instruction to follow and configure yourself, if you need more assistance you can contact us.
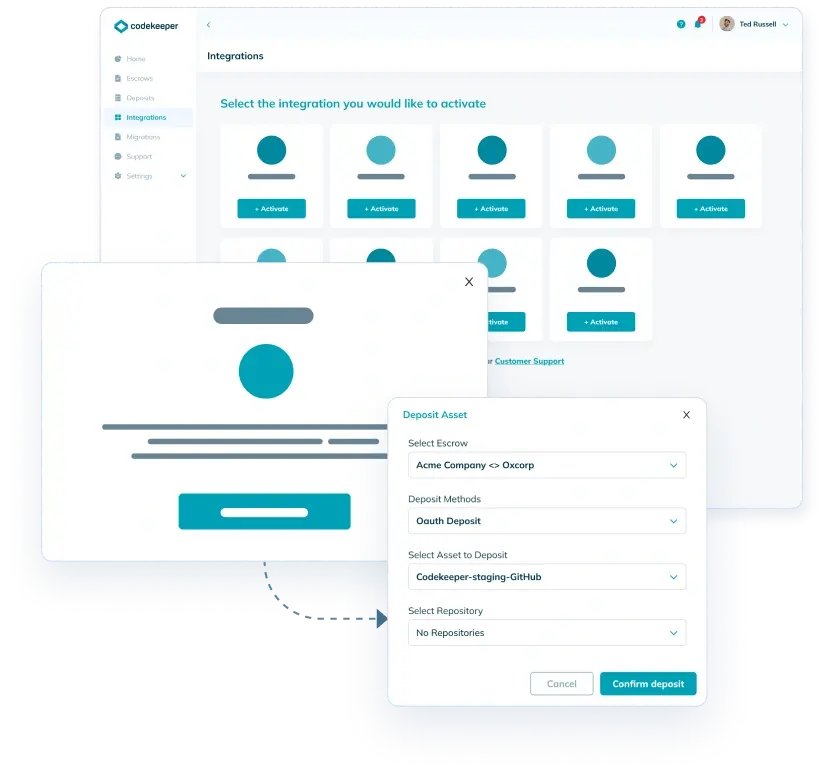
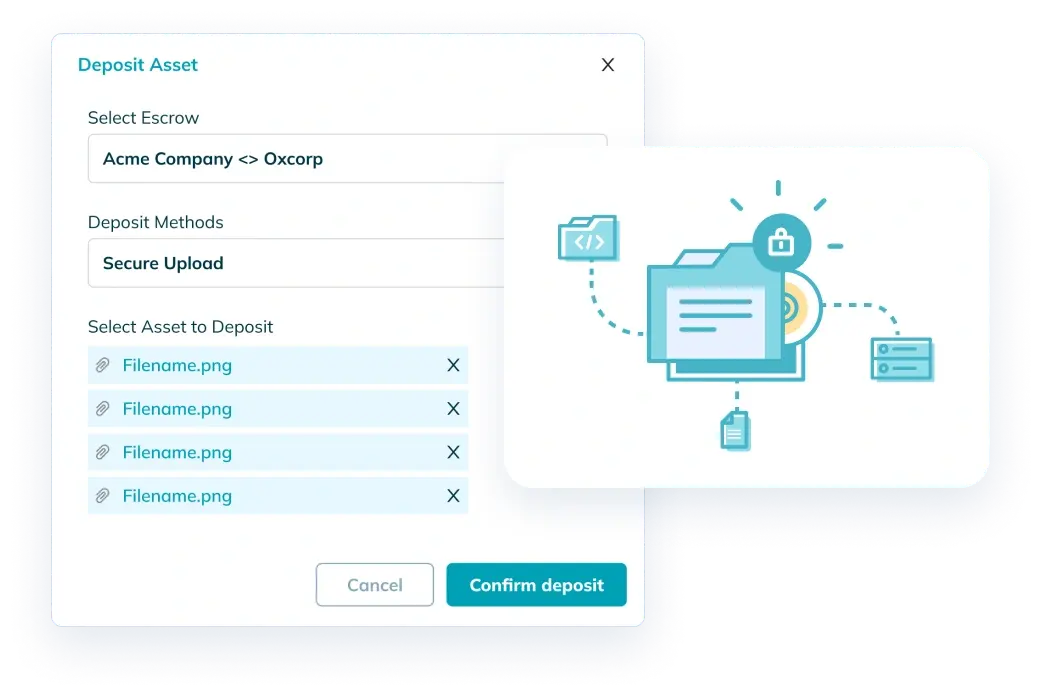
Or go manual and use our secure upload folder process
Our manual upload folder system also provides you with a secure way to deposit your credential information. Just upload your assets and we’ll do the rest!
Not covering your needs yet?
Our team of experts are standing at the ready to assist in finding a solution for your unique needs.

Industry-leading features at the best price
You don’t need to break the bank to protect your assets with unmatched security, scalability, and availability.
We believe in meeting our clients where they’re at. Tell us about your situation and we will tailor an offer to suit your specific needs.
We believe in meeting our clients where they’re at. Tell us about your situation and we will tailor an offer to suit your specific needs.
Securely stored at the best data centers
We operate within the ISO27001 security framework. Our data center certifications:

ISO27001 data security
Our data centers adhere to the highest security standards and security policies. Security is always our first priority.
End-to-end encryption
Data is secured at all times, both in transit and at rest with AES256/512 encryption.
Deposit audit / logs
Review the deposit history on your account.
Secure upload folder
If you prefer manual upload, our upload folder system also provides you with a secure way to deposit your source code.
GDPR compliance (add-on)
If your deposits contain GDPR related data you will probably need a data processing agreement and related services.
HIPAA compliance (add-on)
If your deposits contain HIPAA related data you will probably need a data processing agreement and related services.
Easy & Automated
Other critical software assets you can protect
Automated depositing of all the assets you will need to quickly recover, like the source code, data, information, and configuration scripts.
Source code escrow
Make sure source code is deposited as part of your escrow, so you can redeploy when needed.
Learn more
Data
Most applications require your data to work well. Deposit databases or backups to make sure you don’t lose track of data.
Learn more
Documents
Deposit all kinds of intellectual property, sensitive information, and other critical documents.
Learn more
Technology & designs
Use the escrow to deposit intellectual property that has been developed.
Learn more
Ready for Recovery
Software Escrow — Securely store your software assets, ready for quick recovery
Protect critical software assets
Easy escrow management
Quick recovery
These companies already secured their software continuity. Will you start today?
Software escrow protects your business. It stores your source code with a trusted third party and ensures recovery if a supplier fails to support or provide access to essential software.
Best price guaranteed
No hidden costs
E-BOOK
Software Escrow 101
Fill in the form below to learn how software escrow helps you mitigate software risk and build strong cyber resilience.

**E-book available only in English
Get your free introduction to software escrow
Frequently asked questions
What is credentials escrow?
Credentials escrow is a service that allows businesses to securely store their login credentials, passwords, and other sensitive authentication information with a third-party escrow agent like Codekeeper. This service is used to protect businesses from losing access to critical systems and applications in the event that the original login credentials are lost, stolen, or otherwise become inaccessible.
Why do I need credentials escrow?
Businesses use credentials escrow to ensure that they always have access to their critical systems and applications, even if the original login credentials are lost or stolen. This can be particularly important for businesses that rely on cloud-based services, as it can be difficult or impossible to access these services without the proper login credentials.
How does credentials escrow work?
To use credentials escrow, businesses first need to identify the systems and applications for which they want to store their login credentials. They then work with Codekeeper to create an escrow agreement that outlines the terms and conditions for storing and releasing the credentials. Once the agreement is in place, the business provides Codekeeper with their login credentials, which are securely stored until they are needed.
What are the benefits of credentials escrow?
- Security: A credentials escrow provides a secure way to store sensitive information, such as passwords and cryptographic keys, protecting them from unauthorized access or theft.
- Disaster recovery: In the event of a lost or forgotten password, a credentials escrow provides a way to retrieve and restore access to important systems and applications.
- Business continuity: If an employee leaves a company or is otherwise unavailable, a credentials escrow can ensure that critical business processes can continue without disruption.
- Compliance: A credentials escrow can help organizations comply with security and privacy regulations by providing a secure way to store and manage sensitive information.
- Peace of mind: By using a credentials escrow, individuals and organizations can have confidence that their sensitive information is being stored securely and can be retrieved when needed.
What types of materials can be deposited into credentials escrow?
Credentials escrow typically stores sensitive information related to an individual's identity and authentication, such as passwords, cryptographic keys, security tokens, biometric data, and other forms of credentials used to access computer systems, applications, and networks.
How much does credentials escrow cost?
Pricing starts from $99 per month. For more details, you can explore our pricing options here.
What are the supported integrations?
We support over 50 popular developer platforms and integrations. You can view the list of available integrations here.
How do I get started with credentials escrow?
To get started with data escrow, you can book a demo with one of our experts or directly explore our pricing options here.
What happens to my escrowed materials if Codekeeper goes out of business?
Codekeeper has contingency plans in place to ensure that your escrowed materials remain accessible even in the event that our business is no longer operational.
How secure are the stored assets?
We operate within the ISO27001 security framework and our data centers have multiple certifications to ensure the highest level of security. Deposited assets are encrypted using AES256, ensuring the safety and confidentiality of your software assets.
Can I transfer my existing document escrow agreement to Codekeeper?
Absolutely! We are here to support your needs and will make sure your pre-existing agreement is up to date and implement any additional changes needed during the transfer stage.
Does Codekeeper have access to the content that’s deposited under escrow?
Does Codekeeper have access to the content that’s deposited under escrow?
No. To ensure complete security and guarantee full integrity, the deposited materials are encrypted and stored in an automated process.
What are some examples of credentials escrow release conditions?
What are some examples of credentials escrow release conditions?
Examples of credentials escrow release conditions may include death or incapacitation, change of ownership, termination of employment, inability to access systems, and compliance with legal or regulatory requirements. The specific conditions will depend on the terms of the credentials escrow agreement between the owner of the documents and Codekeeper.
What happens in the event of a release?
Once the release conditions are met, the necessary assets will be made available to the beneficiary.



