Escrow agreements
Solid software escrow agreements for system resilience
Protect your critical software with clear legal frameworks, custom terms, and SLAs drafted by our in-house escrow experts.

Software resilience isn't built on hope or handshakes. Without a clear, enforceable agreement, your software — and the business that depends on it — is vulnerable to delays, disputes, and risk.
Software resilience isn't built on hope or handshakes. Without a clear, enforceable agreement, your software — and the business that depends on it — is vulnerable to delays, disputes, and risk.
What is a software escrow agreement?
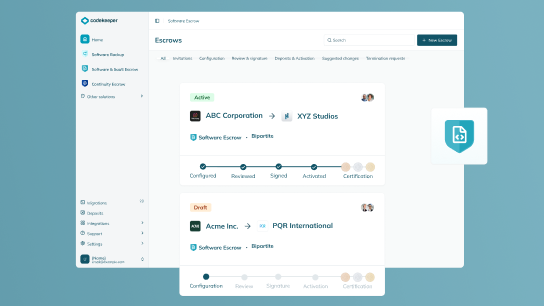
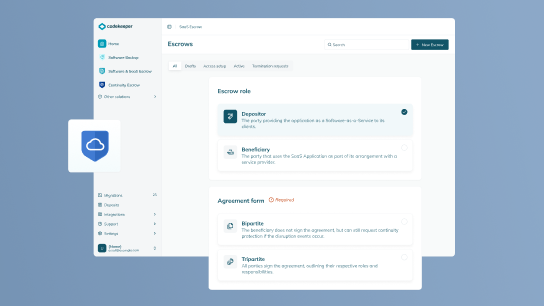
A software escrow agreement is a three-party contract between the software vendor, their client, and a neutral escrow agent. It builds software resilience by defining how and when critical software assets, like source code, are securely released.
This protects everyone involved in the relationship:
Software providers show reliability, reduce legal risk, and meet client requirements.
Clients stay operational even if a vendor fails to deliver, support, or respond.
Both sides work under a clear legal framework that avoids confusion and delays.

It’s a legal arrangement — but not one your team is built to handle
Escrow is legal. It’s also technical, operational, and compliance-critical. And it takes a specialist to bring it all together.
Generic contracts don’t account for technical realities and evolving risks.
In-house legal departments often lack escrow expertise.
Outside counsel takes time and money you may not always have.
Let Codekeeper eliminate your risk with simple, solid software escrow agreements
Agreements delivered by dedicated escrow specialists in under 24 hours
Bipartite, tripartite, and multi-party arrangements
Release terms designed to protect all parties involved
Legal SLAs aligned with your compliance, security, and legal needs
We guard your software, your rights, and your resilience

“Codekeeper really came through for us when we were onboarding an enterprise customer for our SaaS business. Having them in the mix made the customer feel so much more at ease, and honestly, it saved us about 5,000 EUR we didn't have to spend on lawyers to set up the escrow agreement.”
Paul T. *
Senior Managing Director
* Pseudonym used to maintain customer confidentiality.
Ready-to-use software escrow agreement templates for every scenario
No two systems (or agreements) are the same. That’s why we offer purpose-built escrow templates, each mapped to specific business risks, release terms, and compliance needs.
Download "Software licensing sample" for free!
*E-book available only in English
Download "Software development outsourcing sample" for free!
*E-book available only in English
Download "Compliance & regulations sample" for free!
*E-book available only in English
Download "Security & operational resilience" for free!
*E-book available only in English
Download "Transactions, M&A, investment & financing" for free!
*E-book available only in English
Need a custom escrow agreement? We'll draft it for you.
If your escrow needs are complex, multi-party, or bound by specific regulatory frameworks, our legal team will prepare a tailored arrangement to meet your exact requirements.
Create a custom software escrow agreement
Use this form to customize our escrow agreement to your specific situation. Our legal team will review your information and send you a draft agreement that you can modify as needed.

From risk to resilience in 3 simple steps
1. Choose your agreement type
Start with a template or request a fully custom draft based on your situation.
2. Set up your release triggers
We help you define the release conditions, confirm roles, and get signoff from all parties.
3. Make your deposits & activate your escrow
We keep your source code or other agreed-upon assets safe in our digital vaults.
SAMPLE
Fully annotated software escrow agreement
Get a real software escrow agreement with expert annotations explaining every clause, potential risks, and customization options.

*E-book available only in English
Claim your annotated escrow agreement
Explore our escrows by system type
We offer different escrow solutions based on how your software is delivered and what risks you're managing.
SOFTWARE ESCROW
To protect your on-premises software
Escrow source code, data, and docs for long-term access and control.
Learn more
SAAS ESCROW
To secure your cloud apps
Cover code, configs, and dependencies for guaranteed app recovery.
Learn more

CONTINUITY ESCROW
To maintain uninterrupted services
Ensure uptime with hosting and third-party service coverage.
Learn more
Frequently asked questions
What is a software escrow agreement?
A software escrow agreement is a contract between a software provider, their client, and a neutral third party. It defines when and how key software assets, like source code or documentation, can be accessed if something changes in the business relationship.
What are some common trigger events for a source code release?
Common escrow release triggers include missed support obligations, bankruptcy, or an acquisition that affects ongoing access. You define these when setting up your escrow terms.
Do I need a lawyer to draw up my escrow agreement?
No. Codekeeper provides the legal framework and guides you through an escrow setup. You don't need outside counsel unless you prefer it.
Can I customize the terms and conditions of my escrow agreement?
Yes. You can define release triggers, add parties, or align the agreement to meet compliance or operational needs.
Can I include multiple parties in the same agreement?
Yes. Codekeeper supports multi-vendor and multi-client setups, which means you can add more than one beneficiary to a single escrow agreement. These kinds of arrangements are ideal for complex deals, partner networks, or shared platforms.
What makes Codekeeper secure?
Codekeeper operates in accordance with ISO 27001 security standards. All deposits are encrypted using AES256, access is tightly controlled with MFA, and our infrastructure meets global compliance benchmarks.
Can I transfer my existing software escrow agreement to Codekeeper?
Yes, you can transfer your existing software escrow agreement to Codekeeper. We’ll review your pre-existing agreement, make updates if needed, and implement any additional changes needed during the move.
How much does a software escrow agreement cost?
Most software escrow agreements fall between $50 and $5,000 per year, depending on how many applications are covered and whether verification is included. For a single application, Codekeeper plans start at around $99 per month. You can view all plans and options on our pricing page.



