how it works
Protect your business from software failure
Your operations depend on software you don't control. We fix that with escrow solutions that guarantee your software continuity.
What is software escrow — and how does it work?
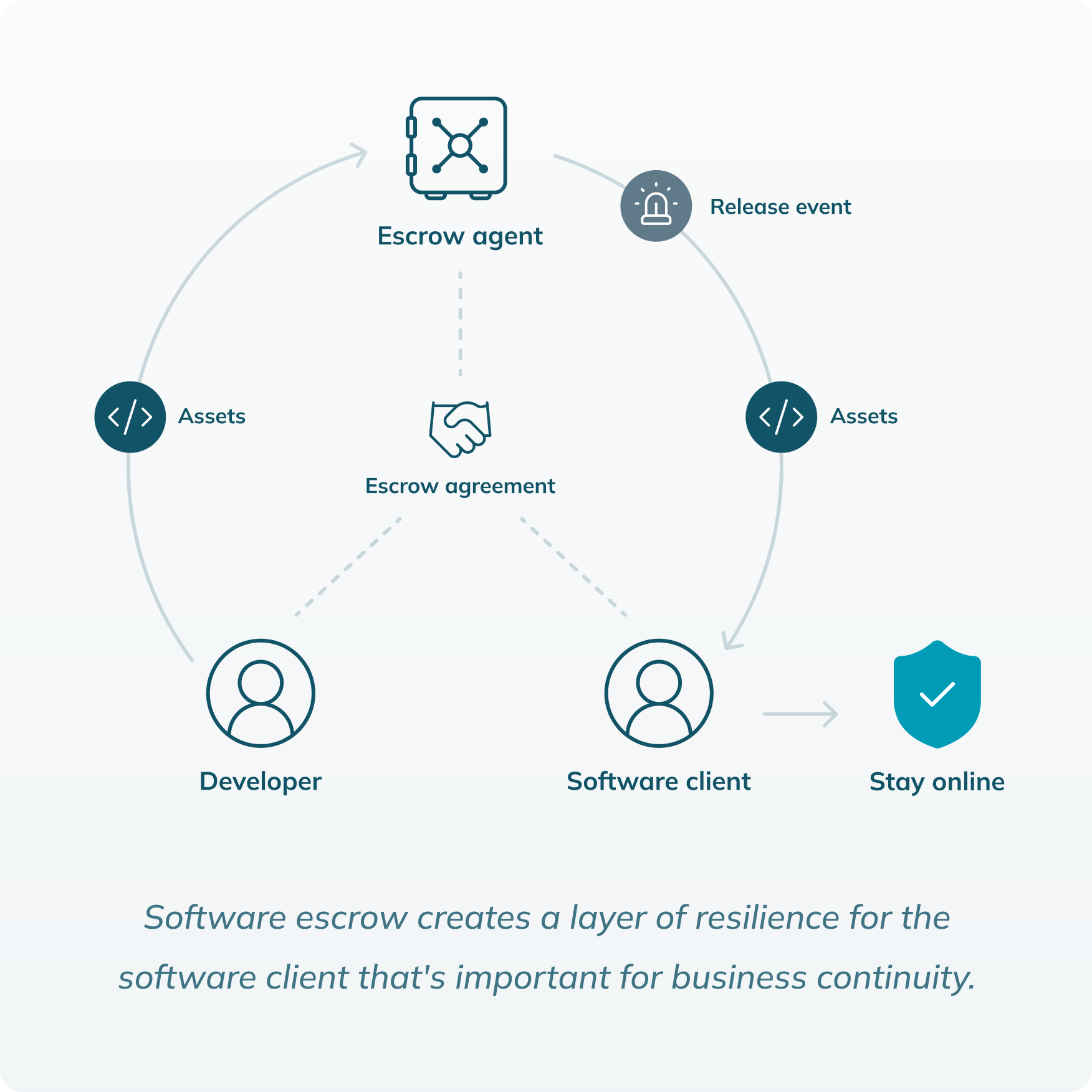
Software escrow is a risk management arrangement where a third party holds critical software assets on behalf of the developer who made the software and the client who uses it.
- Developer gives valuable software assets (source code, etc.) to a trusted third party (escrow agent).
- All parties sign an escrow agreement that defines when and how the materials will be released.
- The escrow agent keeps the escrowed materials safe until something bad happens (release event).
- The escrow agent gives the assets to the software client so they can keep using the software without the original developer’s support.
Break free from software vulnerability
Codekeeper's comprehensive Software Escrow, SaaS Escrow, and Continuity Escrow solutions give you the safety net your business needs. We store your code. But we also create a resilient foundation that keeps your operations running, no matter what.
How we guarantee your software continuity
We've designed a simple five-step process to help you move from software vulnerability to guaranteed operational stability.
1
Book a demo and choose a plan
During an initial consultation, we'll analyze your software ecosystem together to identify which applications truly matter to your operations. This helps us recommend the most appropriate protection options based on your actual needs.

2
Invite your team and establish an escrow agreement
Our in-house legal team handles the entire escrow framework without requiring external lawyers or additional fees. We help you establish clear, transparent terms so you know exactly when and how your code will be released if a trigger event occurs.

3
Upload deposits through automated integrations
We built our platform to work with the tools you already use. The app supports over 50+ integrations, including GitHub, BitBucket, AWS, Azure, and Google Cloud. The system automatically synchronizes your software assets daily and captures changes without creating extra work for your team.

4
Order asset verification
While storing your software is essential, knowing it will actually work during recovery is equally important. Our verification process thoroughly examines everything from source code to configuration files to ensure your deposited assets remain functional and ready for immediate deployment if needed.

5
Earn Software Resilience Certificates
After successfully completing the verification tests, we issue certificates that document your software protection measures. Many clients find these certificates particularly helpful when speaking with auditors, regulators, or other stakeholders who need to understand your preparedness measures.

Get genuine peace of mind
While others worry about vendor failures, you'll operate with confidence, knowing your critical applications are secured, verified, and maintained for uninterrupted business continuity.
Escrow solutions for every software dependency
Our comprehensive software resilience solutions combat all aspects of software risk to help guarantee continuous access to the critical applications that power your business operations.
software escrow
Protection scope: On-premises software
The vendor deposits their source code, data, and documentation into our secure repository. Our platform encrypts these assets and stores them in immutable, access-controlled vaults. When specific trigger events occur, we verify these conditions and release the escrowed assets.
Best for:
Enterprise customers using mission-critical on-premises software
Regulated industries with complex compliance requirements
Organizations with limited in-house technical resources
Development firms looking to build trust with enterprise clients
Learn more
SAAS escrow
Protection scope: SaaS applications
Extend traditional escrow to cover all components needed for SaaS operation. Our 50+ integrations can help you capture source code, container images, infrastructure-as-code configurations, deployment scripts, and third-party dependency information.
Best for:
Businesses relying on cloud software for critical operations
Companies in regulated industries using SaaS solutions
Organizations with robust vendor risk management programs
SaaS companies pursuing enterprise clients
Learn more
continuity escrow
Protection scope: SaaS applications
Set up payment escrow accounts and secure connections to service providers. When you report a missed payment or service degradation, we automatically step in to maintain these services before disruption occurs.
Best for:
Organizations requiring true business continuity
Businesses with complex infrastructure dependencies
Enterprises with strict service-level agreements
Vendors with contractual uptime guarantees above 99.9%
Learn more

Success stories about software resilience
See how our clients transformed software risk into software continuity with Codekeeper.

CASE STUDY
How a Healthcare Network Protected Critical Systems From Vendor Risk
Learn how a vulnerable healthcare network secured their critical patient systems when their vendor faced collapse — with Codekeeper's Software Escrow to prevent operational disaster.
“Software Escrow has become as fundamental to our operational security as data backups.”
Download case study

CASE STUDY
Logistics Provider Maintains 100% Operations With SaaS Escrow When Vendor Disappears
Find out how a logistics company maintained uninterrupted operations after their essential SaaS vendor disappeared — with Codekeeper's SaaS Escrow solution to keep deliveries on schedule.
"The process was surprisingly straightforward — much less disruption than we anticipated."
Download case study

CASE STUDY
How an E-commerce Platform Eliminated Disruptions With Continuity Escrow
Explore how an e-commerce retailer eliminated payment disruptions and boosted customer satisfaction after their processor declared bankruptcy with Codekeeper's Continuity Escrow solution.
“Codekeeper's track record of quick deployment and proven continuity approach won us over.”
Download case study

CASE STUDY
How SaaS Escrow Unlocked Enterprise Deals for a Growing Payment Platform
Discover how a growing payment platform overcame enterprise sales barriers and turned business continuity concerns into a competitive advantage with Codekeeper's SaaS Escrow solution.
"The escrow solution transformed our biggest sales obstacle into a competitive advantage."
Download case study
Don't let software vulnerability threaten everything you've built
When critical software suddenly becomes unavailable, operations halt, revenue stops, and customer trust erodes. Don't wait to discover these vulnerabilities during a crisis when it's already too late to act.
Ready to secure your software continuity?
Take the first step toward guaranteed software continuity by scheduling your free escrow consultation today. Our experts will analyze your specific needs and recommend the most effective protection strategy for your organization.
Frequently asked questions
How does escrow integration work with platforms like GitHub or AWS?
Our system connects directly to your repositories through secure API integrations. After a simple setup process, the platform automatically synchronizes with your development environments on your preferred schedule and captures all changes without manual intervention.
What are the steps involved in a Continuity Escrow solution?
Our Continuity Escrow process starts with a demo where you'll see how we transform software risk into guaranteed uptime. You'll then select your protection tier based on your needs — covering one vendor, multiple providers, or your entire infrastructure. Next, you'll connect your platforms through our app, which supports 50+ automated integrations without complex setups. We then verify your protection is complete and ready for activation. Finally, you receive Software Resilience Certificates as documented proof for auditors, boards, and stakeholders.
Are there automated solutions for escrow deposits?
Yes, Codekeeper offers automated solutions for escrow deposits. Unlike traditional manual systems, our platform connects directly to your repositories (GitHub, BitBucket, AWS, etc.) to automatically capture code, configurations, and dependencies.
How often should escrow deposits be updated?
Deposit frequency should align with your development cycle and risk tolerance. Critical applications typically benefit from daily or weekly updates, while stable systems might require less frequent refreshes. Our automated synchronization makes regular updates simple by connecting directly to your repositories.
How do recovery certificates work in escrow services?
Recovery certificates function as digital proof of your software protection. After completing verification, our system generates a signed Software Resilience Certificate containing details about your escrow status, verification level, and recovery timeline. When regulatory audits or customer due diligence occurs, you simply share this certificate rather than explaining complex technical details.
How can escrow services reduce legal costs?
Traditional escrow setups typically require extensive legal involvement with expensive fees. Our standardized frameworks eliminate this expense with legally vetted templates specific to software protection.



